Enhance SIEM Alerts through Automation
Augments SIEM notifications using MITRE ATT&CK information and connects with Zendesk.
How it works
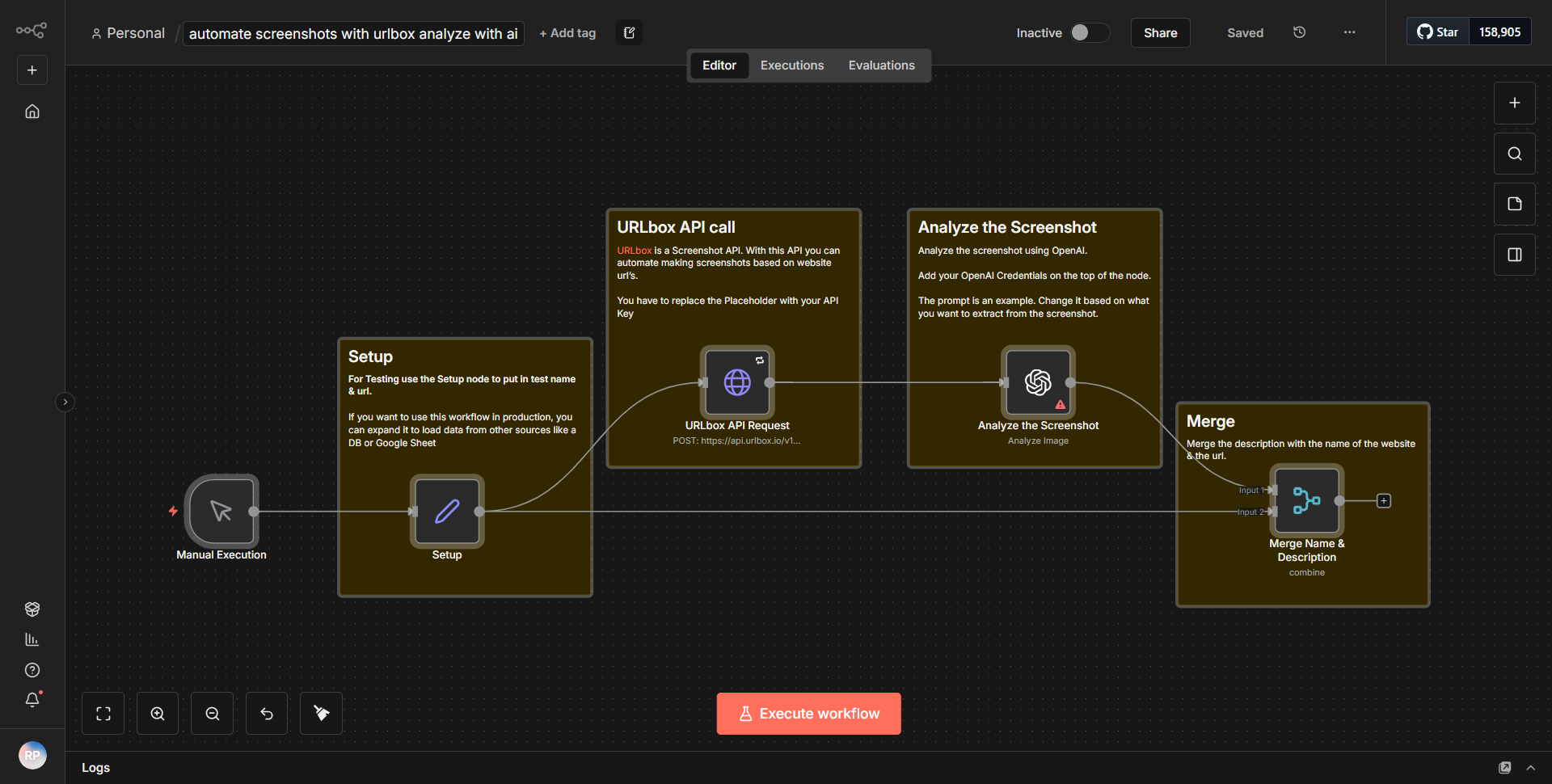
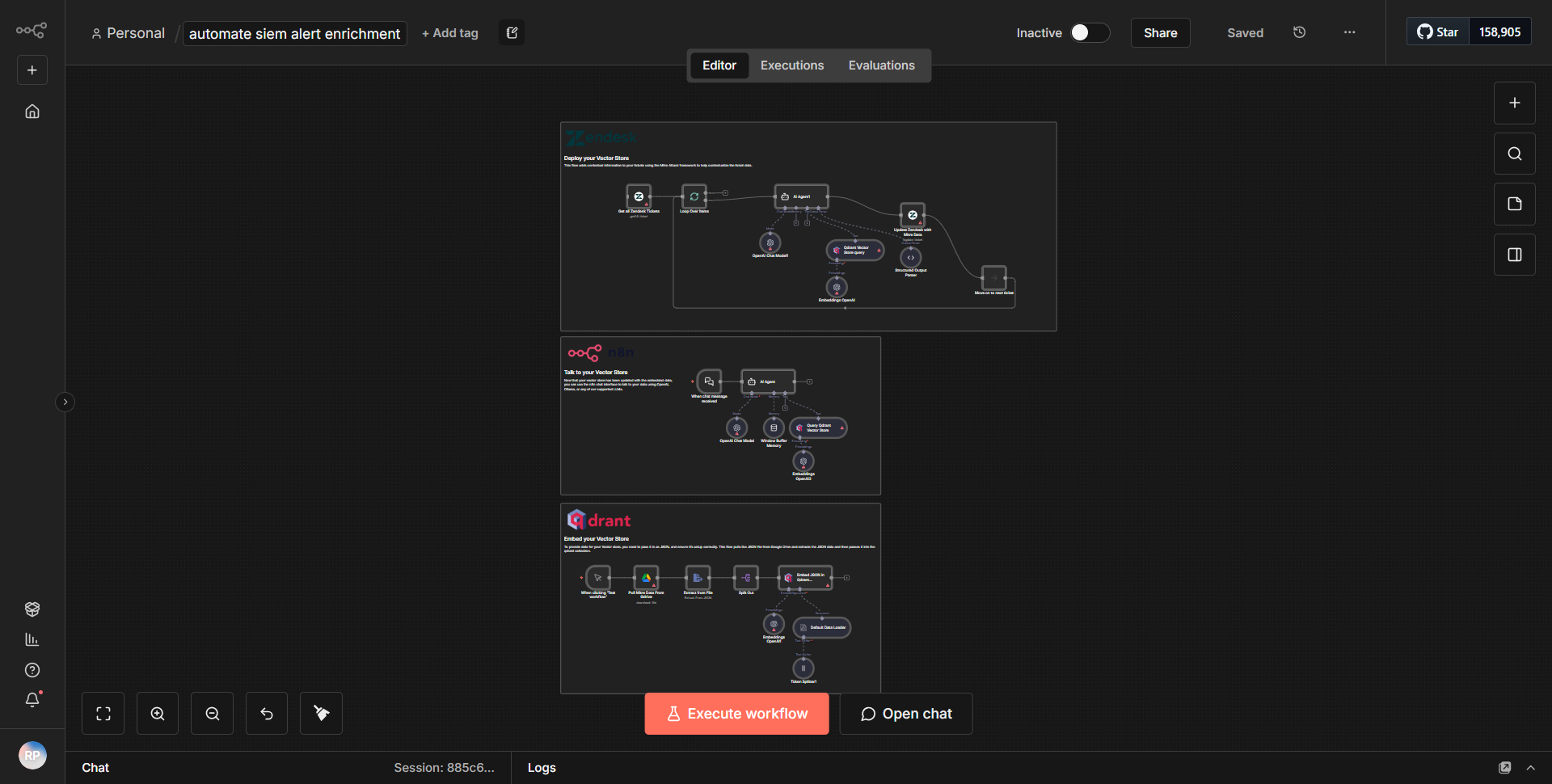
The workflow titled "Enhance SIEM Alerts through Automation" is designed to enrich Security Information and Event Management (SIEM) alerts with contextual information from the MITRE ATT&CK framework and subsequently create tickets in Zendesk for further investigation. The workflow operates in a series of sequential steps, utilizing various nodes that facilitate data retrieval, processing, and integration.
1. Trigger Node:
The workflow begins with a trigger node that activates when a new SIEM alert is generated. This node captures the alert details, including relevant metadata such as the alert type, severity, and timestamp.
2. HTTP Request Node:
Following the trigger, an HTTP Request node is employed to query the MITRE ATT&CK API. This node sends a request to retrieve tactics and techniques associated with the specific alert type identified in the previous step. The response from the API provides valuable context that enhances the alert.
3. Function Node:
The data received from the MITRE ATT&CK API is then processed by a Function node. This node is responsible for formatting the response and extracting key information, such as the relevant tactics and techniques, which will be included in the Zendesk ticket.
4. Zendesk Node:
After processing the data, a Zendesk node is utilized to create a new ticket. The enriched information from the SIEM alert, along with the contextual data from the MITRE ATT&CK framework, is included in the ticket description. This ensures that the support team has all necessary information for effective incident response.
5. End Node:
Finally, the workflow concludes with an End node, signaling the completion of the process. This node ensures that all operations have been executed successfully and that the workflow can be triggered again for subsequent alerts.
Key Features
- Automated Enrichment:
The workflow automatically enriches SIEM alerts with contextual information from the MITRE ATT&CK framework, providing security teams with deeper insights into potential threats.
- Integration with Zendesk:
By creating tickets in Zendesk, the workflow streamlines the incident response process, allowing support teams to track and manage alerts effectively.
- Real-time Processing:
The workflow operates in real-time, ensuring that alerts are processed and enriched as soon as they are generated, which is critical for timely incident response.
- Customizable:
The workflow can be easily modified to accommodate different alert types or additional data sources, making it adaptable to various organizational needs.
Tools Integration
- MITRE ATT&CK API:
The workflow integrates with the MITRE ATT&CK framework to fetch relevant tactics and techniques associated with SIEM alerts.
- Zendesk:
The workflow uses the Zendesk node to create and manage support tickets, facilitating communication and tracking of security incidents.
- n8n Nodes:
The specific nodes utilized in this workflow include:
• Trigger Node (for SIEM alerts)
• HTTP Request Node (to query the MITRE ATT&CK API)
• Function Node (for data processing)
• Zendesk Node (to create tickets)
API Keys Required
- MITRE ATT&CK API Key:
If the API requires authentication, an API key or token will be necessary to access the MITRE ATT&CK framework.
- Zendesk API Credentials:
To create tickets in Zendesk, valid API credentials (such as an API key or OAuth token) are required.
• If no API keys or credentials are needed for any of the services, this should be clearly indicated.